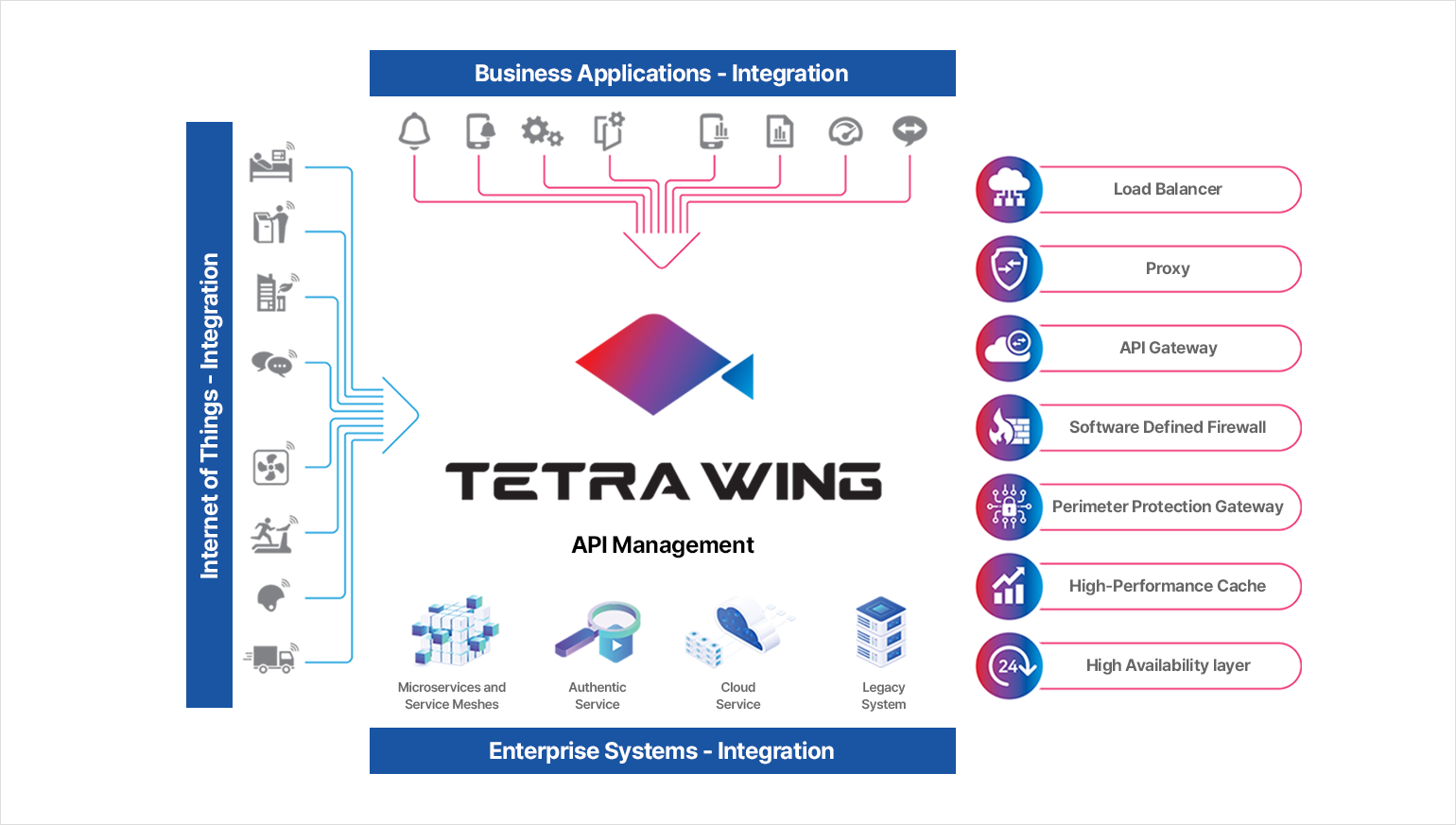
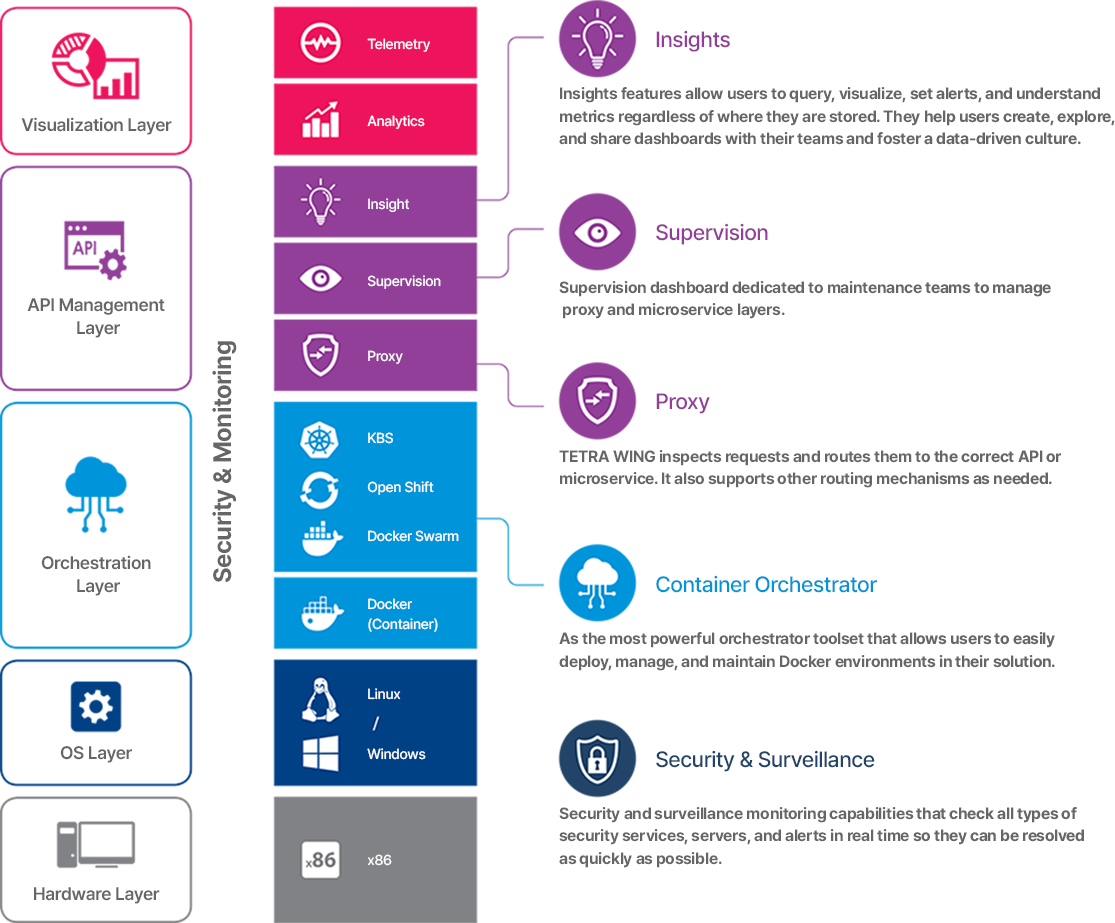
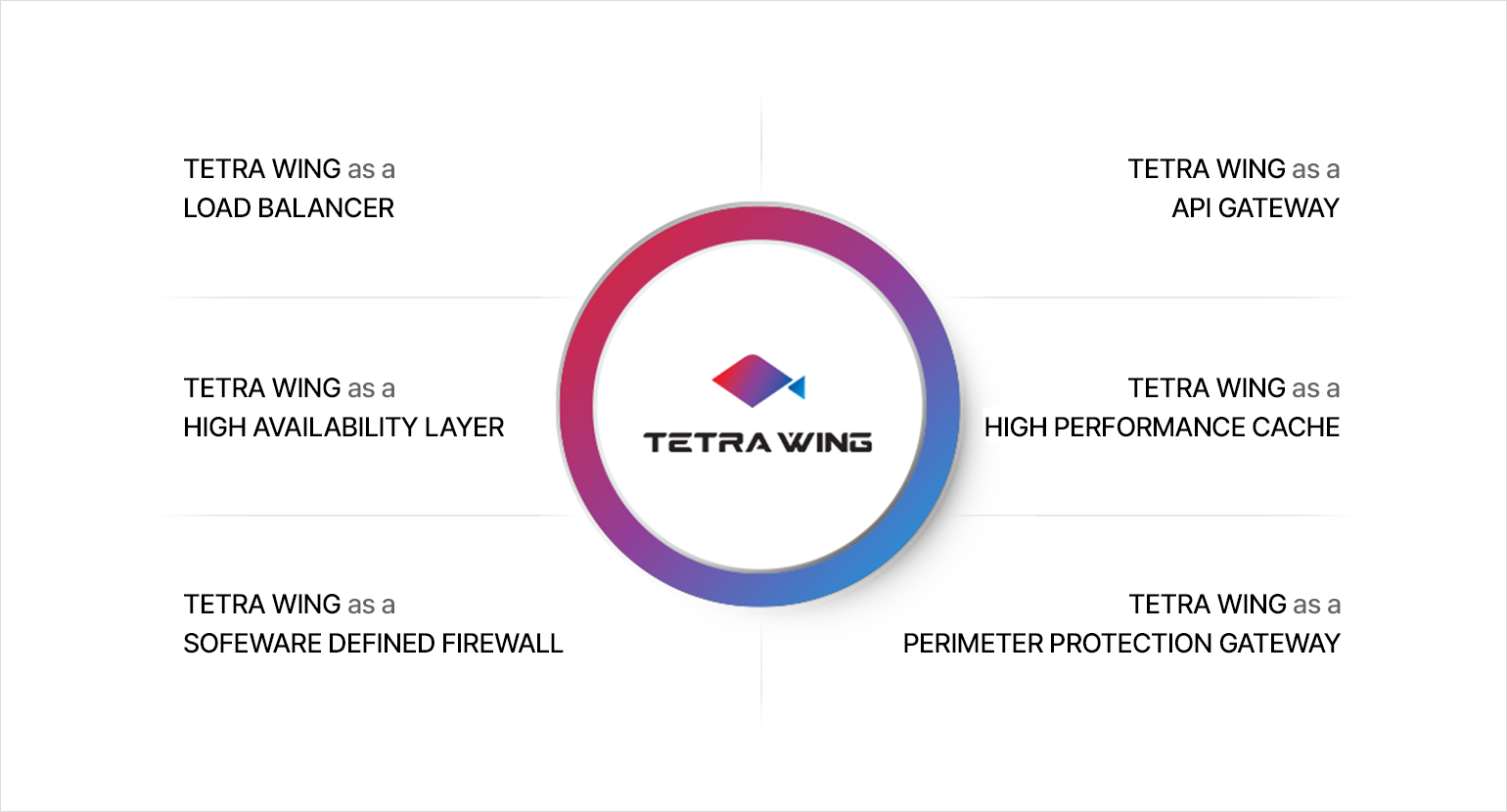
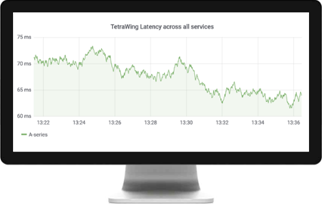
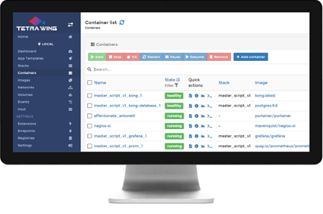
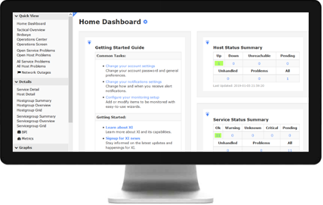
TETRA WING INTRODUCTION
Microservices act as the basis for the development and improvement of new applications in a manner that is quicker and easier than the existing monolithic method. They are a total solution that allows companies to implement next-generation MSA. Microservices and APIs are both needed to effectively implement these next-generation architectures.
TETRA WING defines an API (application programming interface) management solution suitable for any company. It provides unprecedented scale and real-time customer experience for the high-performance data exchange requirements of companies and government agencies.