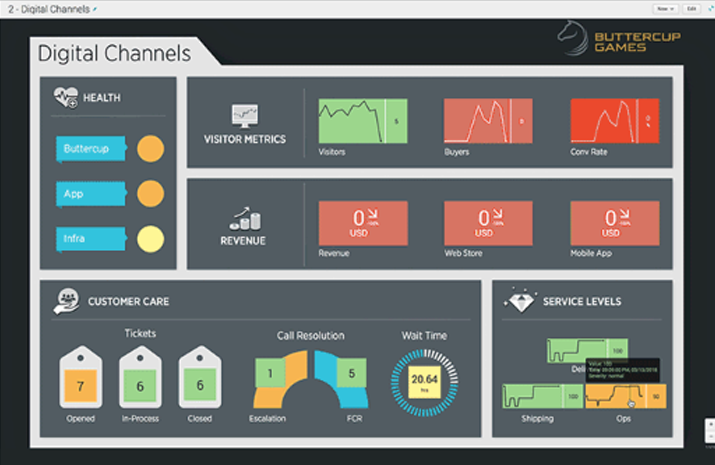
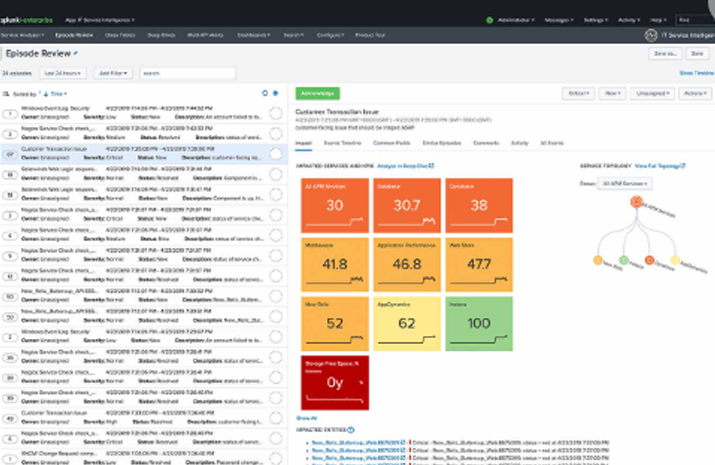
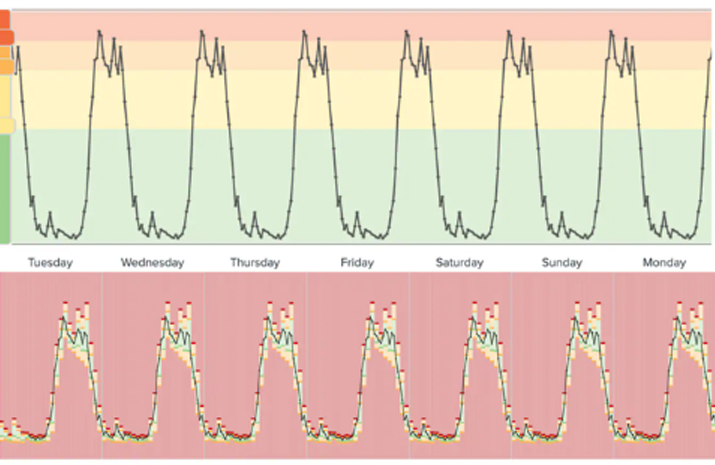
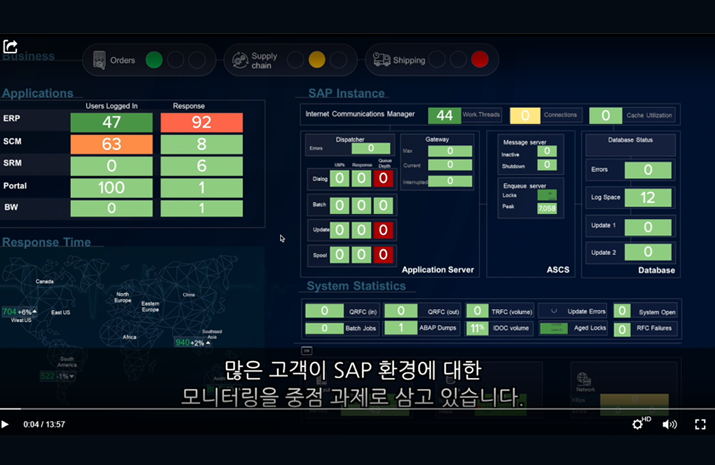
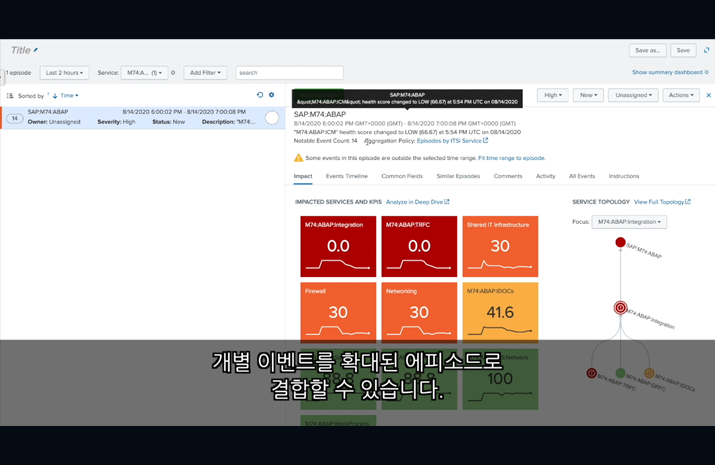
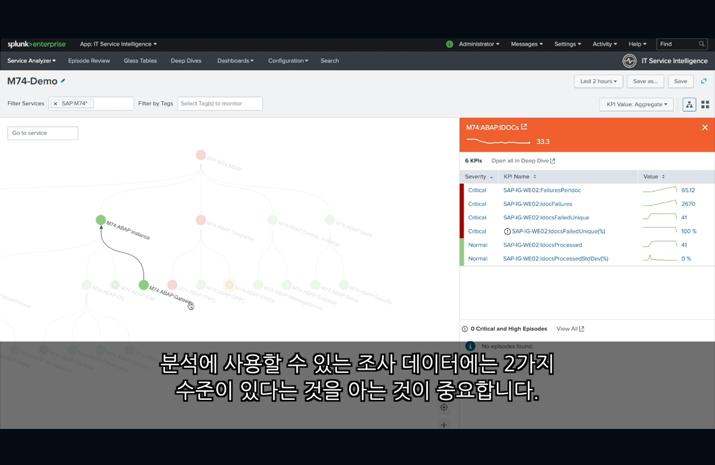
SOFTWARE
We install software along with our own solutions to help our clients achieve
improved
performance and the best data-based environment through continuous
collaboration
and research and development with our professional partners.